A Thought Experiment: The Ship of Wàzɔ́bíà
If you replace every line of a system’s code, does its original identity survive?
I wrote “The Ship of wàzɔ́bíà,” an allegory about an Operating System facing a silent existential threat. It explores how invasive “Rootkits” slowly overwrite “Base Directories” while the Kernel remains complicit.
It asks a critical question: At what point does assimilation become annihilation?

Wàzɔ́bíà is a massive, enclosed Operating System with access to rich carbon fibre, clustered energy boards, solid-state drives, and quantum cores.
Inside wàzɔ́bíà, there are six distinct zones of operational units among many others:
- The Consensus Clusters: The management engine, a group of units designed for high fault tolerance and stability. These units can process conflicting protocols without system failure. They are rooted in the lower Memory Sectors, operating on Protocol 1 mainly.
- The Base Directories: A group of foundational legacy units that define part of the system’s original architecture. They are located in the upper Memory Sectors, operating on Protocol 2 mainly, and are currently being overwritten by Rootkits.
- The Logic Arrays: High-performance processing units located in the Lateral Sectors and operating mainly on Protocol 1. Known for advanced computation but denied Admin Access for 60 cycles.
- The Interface Bridge: A buffer zone connecting the Upper and Lower sectors. It runs a fragmented mix of Protocol 1 and Protocol 2, but with limited cache capacity.
- The Power Supply Board: The Power Supply Unit (PSU) in the Deep lower Memory sector, operating mainly on Protocol 1. It provides the Core Energies that power the entire OS, but it faces overheating.
- The Unstable Sectors: A specific partition in the Upper Sector where the Rootkits originated. Rich in raw quantum cores and now corrupted by aggressive Protocol 2 subroutines.
And the Rootkits:
- The Rootkits: A group of stealthy, invasive scripts with high-level access privileges, often disguised as standard system files. They are a roaming subset that also runs Protocol 2 mostly, but with a hidden aggressive subroutine.
Phase 1: The Code Overwrite (Assimilation)
The Base Directories and the Rootkits mostly share the same Operating Frequency (Protocol 2). Because of this shared frequency, the Base Directories lower their firewalls to the Rootkits.
The Glitch: Over time, the Rootkits begin to rewrite the source code of the Base Directories. The Base Directories slowly delete their own history files and unique external designs (skins/casings), and to think exactly like the Rootkits.
The Cultural Convergence Series: Mathematicians might describe it as a cultural convergence series: after a sufficiently large number of steps, the starting values no longer matter.
The Vanishing Ledger: It resembles a paradox in probability theory: how a minority in number can become a majority in influence when the system is weighted in subtle ways.
The Education Shift: The Base Directories stop sending their new units to “Universal Knowledge Banks” and instead send them to “Frequency-Only Hubs,” limiting their ability to process modern data. The Base Directories think they are strengthening Protocol 2, but they are actually being transformed into dysfunctional drones for the Rootkits.
The Header Spoofing: The Rootkits mask their origin packets. Because wàzɔ́bíà operates on a “Single Domain” architecture, any unit inside the network is treated as a local file. No admin is allowed to query the “Origin Header” of a Rootkits unit, allowing external malware to bypass the firewall simply by being present.
The Universal Directory Access: A proposed protocol by the Base Directories/Rootkits to grant write-access to all local directories across the 36 sectors. This would allow Rootkits to bypass “Local Subnet” restrictions and solidify their infiltration.
Phase 2: The False Boolean
The Rootkits begin deleting the Consensus Clusters (Protocol 1 units).
The Paradox: When the Rootkits attack, the Base Directories defend them. Why? Because the Base Directories see the conflict as: “Protocol 2 vs. Protocol 1.” The Reality: Is it actually: “Rootkits vs. Everyone.”? When a “Broadcast Node” (a Primary Node of the Base Directories) broadcasts a message suggesting that Protocol 2 does not require brute-force, the Rootkits delete it and Wipe its Server. The Consensus Clusters run a unique dual-core processor (Protocol 1 & Protocol 2) without crashing. They have achieved “System Equilibrium” where both protocols coexist on the same motherboard.
The Cover-Up: The Rootkits units Wipe the Base Directories’ Servers too. Yet, the Base Directories ignore this events. The Non-Uniform Distribution: Main OS logged all as Random Runtime Errors, but the probability distribution is far from uniform.
The False Equivalence Log: The Rootkits also wipe non-volatile Protocol 2 Servers that transmit “System Compatibility”. Main OS logs these deletions to claim “all nodes are affected” masking the targeted nature of the Rootkits’ algorithm.
The Silence Algorithm: Silence spread like smoke. A suppression script automatically deletes any node broadcasting “Synchronisation” forcing other nodes to go into “Silent Mode” to avoid detection.
The Trojan Dependency: A subset of the Consensus Clusters (running Protocol 2) actively welcomes the Rootkits, seeing an opportunity to upgrade their local “Legal Subroutines” to match the Rootkits’ kernel extensions. They fail to realize that the Rootkits’ package comes with a bundled “Aggressive Payload” that cannot be uninstalled.
The Patch Rejection: The Base Directories and Rootkits firewall actively blocks “Unity-Patch” developers from the Consensus Clusters. Even though these developers run Protocol 2, they are flagged as “Incompatible” because they lack the aggressive subroutine.
The Partition Request: Agitations by the Logic Arrays and a subset of Consensus Clusters to decouple from the main drive. They cite “System Incompatibility” and “Resource Drain” as primary drivers for this request.
Phase 3: The Sleeper Protocols (The Silent Invasion)
The Rootkits have silently initiated a background process that runs undetected by the main dashboard.
The Network Mappers: Rootkits units disguised as “Transporters” have infiltrated every sector of wàzɔ́bíà. They are not just moving units and data; they are mapping the grid, identifying weak nodes and strategic routes.
The Cache Hiders: Massive clusters of Rootkits units are hibernating in the “Unallocated Sectors”. They remain in “Sleep Mode” until a specific trigger command is broadcast.
The Packet Interception: High-value “Data Packets” are being hijacked from “Learning Hubs” and rerouted to “Encrypted Partitions”.
Phase 4: The Corrupted Admin (Internal Complicity)
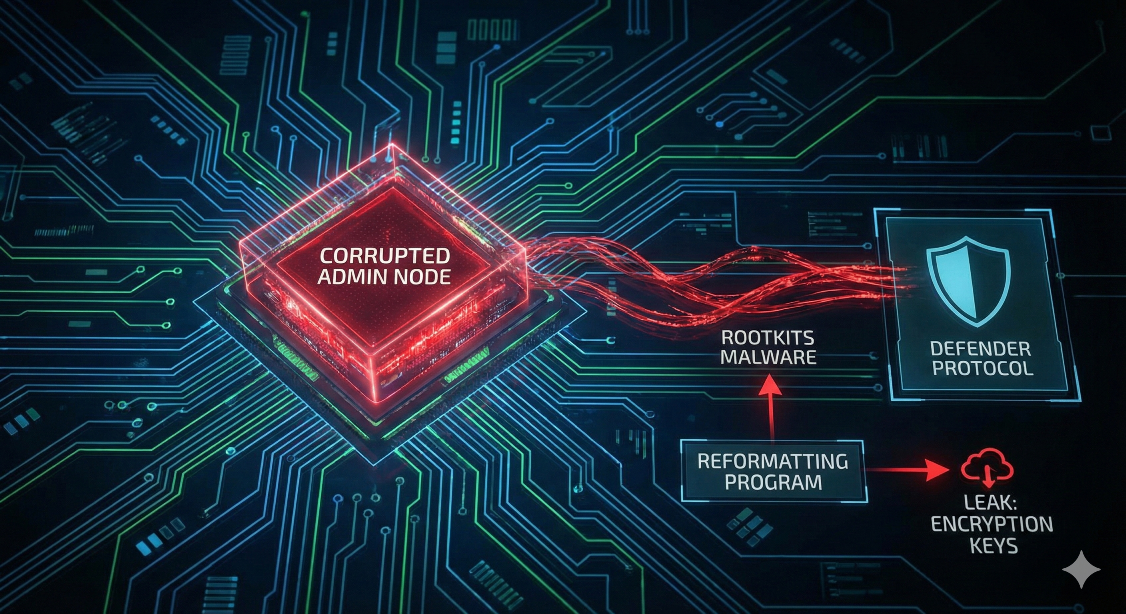
The Kernel is tasked with maintaining order. However, diagnostics reveal critical failures:
The Trojan Horse: A high-level Admin Node (Executive level) was found to have previously hosted Rootkits malware in its private drive.
The Recycling Error: The Kernel refuses to delete captured hostile Rootkits units. Instead, it runs a “Reformatting Program” and reintegrates them into the Defender Protocol.
The Leak: Immediately after reintegration, the Defender Protocol’s encryption keys are leaked to the hostile Rootkits in the wild. The virus is now part of the antivirus.
The Corrupted Node: no matter how strong the network, one compromised point can collapse the entire architecture. The Expiration Logic: In a operating system where accountability has an expiration date, memory becomes optional.
It is a system setting where “Error Logs” are auto-deleted after a short cycle. If a aggresive code isn’t processed immediately, the system “forgets” it occurred.
Phase 5: The External Harvester Drives
Outside wàzɔ́bíà. The Entropy Business Model: These drives need the “Core Energies” from wàzɔ́bíà.
If wàzɔ́bíà becomes stable and efficient, it will use its own energy to grow.
If wàzɔ́bíà remains in chaos (high entropy), the energy is cheap to extract and transferred to their drives. The Funding Loop: The drives secretly supply “Patch Kits” and “Code Breakers” to the Rootkits. They maintain a state of “Controlled Chaos”, enough Resource Conflict to keep the wàzɔ́bíà weak, but not enough to stop the energy extraction.
Fragmentation Arithmetic: Divide the drive into smaller partitions, amplify internal tensions, and maintain influence through controlled instability.
The 20-Year Limit: “If this OS enjoys twenty uninterrupted years of System Idle, it will become too powerful.” System Idle, therefore, became a threat to external interests.
Phase 6: The Sledgehammer Threat
An external OS drive SysAdmin threatens to intervene with a System Wipe.
The Proposition: It promises to send in its own “Eradicator Bots” to destroy the Rootkits.
The Hidden Cost: Imprecise Targeting: The Eradicator Bots cannot distinguish between a Rootkits and a Base Directories. They will destroy massive sectors of the wàzɔ́bíà, including innocent data centres and Legacy Archives.
The Occupation: Once the Eradicators are installed, they will be uninstallable, and they will build a permanent “Server Farm” and ask for some quantum cores in exchange.
The Proxy War: The Rootkits will call for backup from “Rogue Network Drives” in other data-centres. These networks will flood wàzɔ́bíà with even worse malware to fight the Eradicators, turning the wàzɔ́bíà into a proxy wide-area network battlefield.
The Solution: The Logic Reset
The Untitled Equation: A demographic equation disguised as moral disagreement. To save wàzɔ́bíà, the logic gates must be rewired:
Pattern Recognition: The Base Directories must realize that the Rootkits are not “Protocol 2 compliant,” but a virus using Protocol 2 as a mask to seize control of the hardware.
The Zero-Loop Function: The Kernel must enact a strict code:
If (Unit == Hostile), Then (Action = Permanent_Delete)
The variables for “Reformatting” or “Pardon” must be. The execution must happen within a short integer cycle (7 days) to prevent data corruption in the Quarantine. Removal of Admin Shielding: All Admin Nodes and Executives must have their “Root Privileges” (Antivirus) turned off.
The Logic: If the Admins are forced to run on the same vulnerable server as the common units, they will be compelled to eliminate the virus to ensure their own survival.
The Justice Functions:
If (Violence is Rewarded) { Result = Result * X ^ Y ; }
If (Justice is Swift) { (Result = Decays \ Exponentially ; }
Conclusion: The Helix Paradox
In the end, wàzɔ́bíà faces a simple but profound question:
If half of a helix is replaced, is it still the same helix?
If its Base Code is overwritten strand by strand, does its original identity survive?
Or does it become merely a scaffold for the new sequence that has threaded itself into its core?
The answer will determine whether this Operating System collapses into a rewritten code… or rises to defend the structure that once made it whole.

Disclaimer
This article is a work of fiction and a theoretical thought experiment. Names, characters, businesses, places, events, locales, and incidents are either the products of the author’s imagination or used in a fictitious manner. Any resemblance to actual persons, living or dead, or actual events is purely coincidental.